Public Cloud – Flexible Engine
Identity Access Management (IAM) – manage and control access to user identities
Manage user accounts (employees, systems or applications) and control the operating rights of these accounts on their resources

Identity and Access Management (IAM) is a cloud resource management system.
If several users in an organization work collectively on resources, the IAM prevents these users from sharing their account keys with other users and allows security administrators to give users only the necessary permissions. IAM also ensures account security and reduces security risks to corporate information by allowing users to define credential verification rules, password rules, and an Access Control List (ACL).
Basic service
IAM is a central service of the cloud solution. Other cloud services of the cloud solution depend on IAM for authentication.
Figure 1: Position of the IAM in the cloud solution
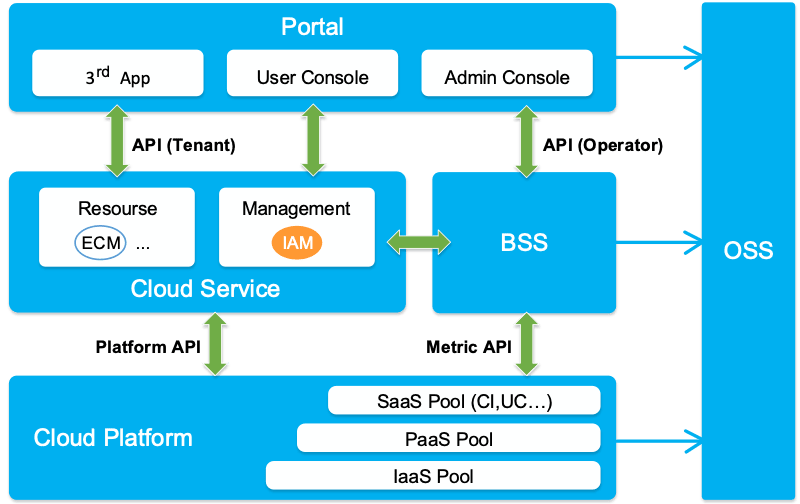
Product Architecture
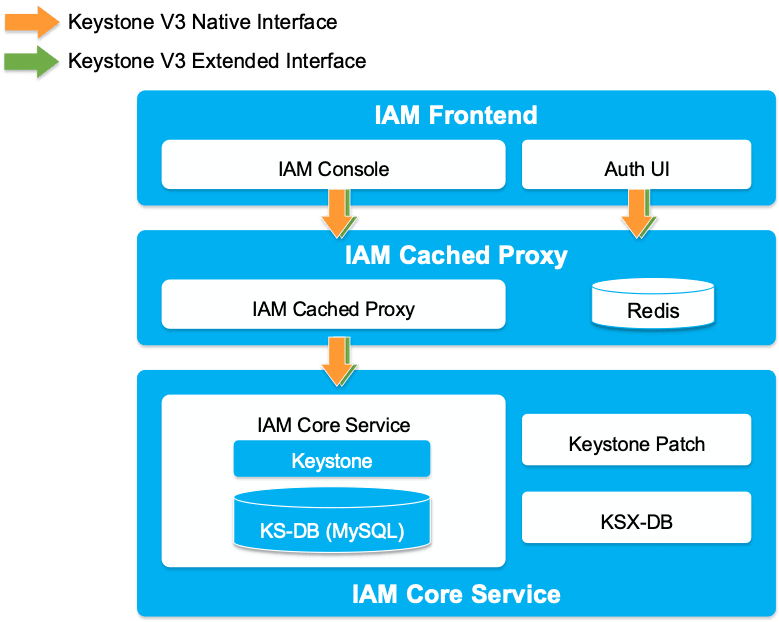
The cloud solution is based on OpenStack. IAM is based on the OpenStack Keystone service.
- IAM Interface: provides user interfaces for authentication and account management.
- Cached Proxy: locally routes and accelerates the main service.
- Basic IAM Service: Uses the Keystone service to implement new features.
Figure 2 : IAM architecture
Benefits
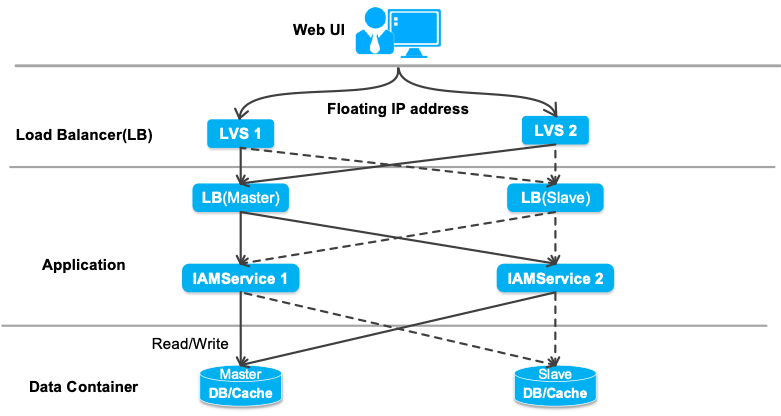
High reliability
In the event of a failure, the IAM enables key services to be restored automatically and quickly using layer-based hot-swap.
Security
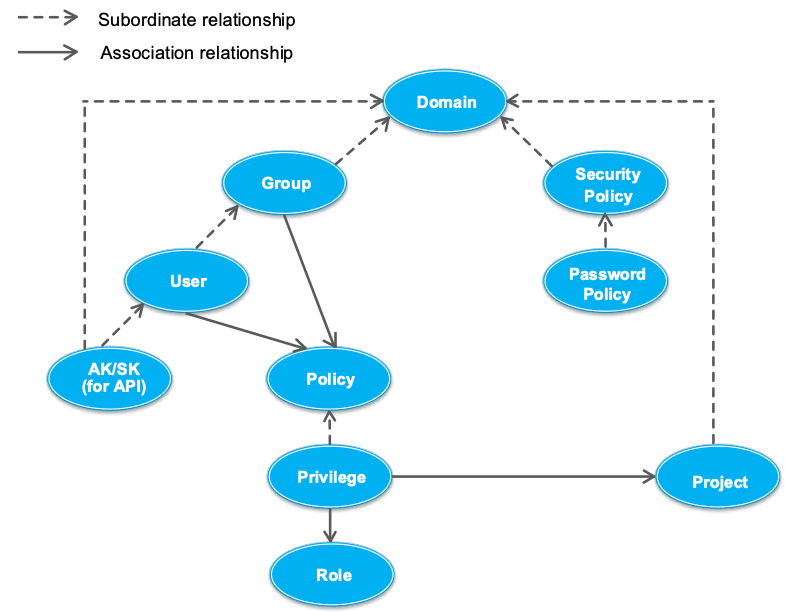
User permissions are managed by user groups, achieving minimum authorization and ensuring the security of cloud resources.
ID verification rules, password rules and ACL can be defined to ensure the security of user accounts and systems.
When a user calls an API, an access key is used to authenticate the user’s identity to improve system security.
Open APIs
Users can develop and access the cloud service system using IAM’s open APIs.
Flexible connection modes
Features
IAM provides the following features :
| Category | Function | Description |
|
Cloud resource security management |
Management of security certificates |
Each user’s security key can be created and deleted in Orange Cloud for Business. Users are authorized to use their security keys to access cloud resources via open APIs. |
|
Management of user access rules |
The IAM service controls user access policies in Orange Cloud for Business. Policies include defining an ACL to limit malicious access to unapproved networks and disabling certain unsecured users to access the cloud service system. |
|
|
User rights management |
An enterprise administrator can define users’ rights to use cloud resources based on their responsibilities. | |
|
User management |
An enterprise administrator can create users based on scenarios. User responsibilities vary depending on the scenario. |
|
|
Federated identity authentication |
A corporate administrator can create a Corporate Identity Provider. The Corporate Identity Provider provides identity authentication for company employees during day-to-day operations. Corporate employees can switch to the Orange Cloud for Business system on the corporate network using the SAML SSO protocol. |
|
|
Temporary certificate AK/SK |
Obtain the temporary access key and the security key via AssumeRole, regular token or federated token. |
|
|
Project Management |
A security administrator can create projects in a region based on department or project requirements and grant permissions on different projects to users. Users can purchase cloud service resources in authorized projects to implement resource isolation management. The security administrator can also contact OCB customer service to define and modify the number of items created in the area. |
Use Cases
Enterprise rights management
When managing the company’s employees, rights to use cloud resources must be assigned to the appropriate personnel to ensure minimum operating rights for the company’s cloud services, prevent unauthorized operations, and reduce the security risks to the company’s information.
User management
API users are used only for API access. Login users are used for password-based login to the console. An enterprise administrator must create users based on scenarios to ensure that API users and logon users are isolated from each other. This feature prevents unauthorized operations and reduces security risks to corporate information.
Federation Authentication
An enterprise administrator can use his company’s IdP to complete authentication and authorization of employee identities, as well as implement single sign-on of his own Web site and the Orange Cloud for Business system, instead of repeatedly creating employee information using the IAM service of the Orange Cloud for Business system.
User Security Policies
Users can define login verification policies, password policies, and ACL to prevent unauthorized users from accessing the system and ensure the security of user information and system data.
Account information management
Users must regularly update the email address, cell phone number and password associated with their accounts to ensure the security of account information.
Open API authentication
When users manage cloud resources using open APIs, they must provide the project IDs and access keys required for authentication.