NSX-T : Create VPN Ipsec
Objective
About IPsec VPN and how to configure an IPsec VPN with VMware NSX Manager (for vCoD Customers only).
Glossary
AH Authentication Header: protocol part of the IPsec suite.
ESP Encapsulation Security Payload: protocol part of the IPsec suite.
IKE Internet Key Exchange: key exchange protocol.
VPN Virtual Private Network: virtual private network.
IETF Internet Engineering Task Force: organization at the origin of Internet standards.
NAT Network Address Translation: network address translation mechanism.
TLS Transport Layer Security: application layer security protocol.
SSL Secure Socket Layer: obsolete version of TLS.
OSI (Open Systems Interconnection) model is a conceptual framework that standardizes the functions of a telecommunication or computing system into seven layers.
About IPsec VPN
Internet Protocol Security (IPsec) is a broadly used network layer (“Internet” layer of the TCP/IP stack or layer 3 “network” of the OSI model) security control for protecting communications. IPsec is a framework of open standards for ensuring private communications over Internet Protocol (IP) networks.
Internet Protocol Security (IPsec) is a suite of open standards for ensuring private communications over public networks. It is the most common network layer security control, typically used to encrypt Internet Protocol (IP) traffic between hosts in a network and to create a virtual private network (VPN). A VPN is a virtual network built on top of existing physical networks that provides a secure communications mechanism for data and control information transmitted between computers or networks. IPsec is also used as a component that provides the security for many other internet protocols.
IPsec is a network layer security protocol with different components:
Encapsulating Security Payload (ESP) is the protocol that transports the encrypted and integrity-protected network communications across the network. If only integrity protection is needed without encryption, the ESP protocol can use NULL encryption. An older method for IPsec transport of non-encrypted data involves the use of the Authentication Header (AH) protocol, but this method is no longer recommended by this guidance.
Internet Key Exchange (IKE) IPSec uses the Internet Key Exchange (IKE) protocol to facilitate and automate the SA setup and the exchange of keys between parties transferring data. Using keys ensures that only the sender and receiver of a message can access it. IPSec requires that keys be re-created, or refreshed, frequently so that the parties can communicate securely with each other. IKE manages the process of refreshing keys; however, a user can control the key strength and the refresh frequency. Refreshing keys on a regular basis ensures data confidentiality between sender and receiver, the current version is IKEv2 defined in RFC 7296.
Authentication Header (AH) AH provides authentication and integrity, Although AH protects the packet’s origin, destination, and contents from being tampered with, the identity of the sender and receiver is known. In addition, AH does not protect the data’s confidentiality. If data is intercepted and only AH is used, the message contents can be read.
The RFCs related to IPsec make the support of AH by the equipment implementing IPsec optional while that of ESP is mandatory. Generally speaking, compared to ESP, AH can be considered obsolete and with a weak contribution from the point of view of security, thus it is generally not implemented.
IPsec Modes
There are two ways that IPsec can function: Tunnel Mode and Transport Mode.
The tunnel mode provides the expected service in most cases.
| IPsec Tunnel mode | IPsec Transport mode |
| Two IP headers are transmitted here. The IPsec policy that safeguards its contents is chosen by the inner IP packet. | The IPsec policy that will be applied to the packet is determined by the IP addresses in the outer header. |
| The contents of the inner IP packet are subject to IPsec policy. | IPsec policy can be determined by the IP header, the next header, and any ports that the following header supports. |
| Both the payload and the IP header of the original packet are enclosed in a new IP packet. | A fresh AH or ESP header is made and added immediately after the initial IP header, depending on the protocol being used. |
| The tunnel mode supports NAT traversal. | The transport mode does not support NAT traversal. |
| For instance, ASA firewalls or Cisco routers. | For instance, a Remote Desktop or Telnet session. |
IPsec VPN Session
Internet Protocol Security (IPSec) VPN secures traffic flowing between two networks connected over a public network through IPSec gateways called endpoints. NSX Edge only supports a tunnel mode that uses IP tunneling with Encapsulating Security Payload (ESP). ESP operates directly on top of IP, using IP protocol number 50.
IPSec VPN uses the IKE protocol to negotiate security parameters. The default UDP port is set to 500. If NAT is detected in the gateway, the port is set to UDP 4500.
IPSec VPN service is supported on Tier-0, Tier-0 VRF, and Tier-1 gateways.
NSX Edge supports a policy-based or a route-based IPSec VPN.
| Policy-Based IPsec VPN | Route-Based IPsec VPN |
| Policy-based IPSec VPN requires a VPN policy to be applied to packets to determine which traffic is to be protected by IPSec before being passed through the VPN tunnel. | Route-based IPSec VPN provides tunneling on traffic based on the static routes or routes learned dynamically over a special interface called virtual tunnel interface (VTI) using, for example, BGP as the protocol. IPSec secures all the traffic flowing through the VTI. |
| This type of VPN is considered static because when a local network topology and configuration change, the VPN policy settings must also be updated to accommodate the changes. | Route-based IPSec VPN is similar to Generic Routing Encapsulation (GRE) over IPSec, with the exception that no additional encapsulation is added to the packet before applying IPSec processing. |
| When using a policy-based IPSec VPN with NSX , you use IPSec tunnels to connect one or more local subnets behind the NSX Edge node with the peer subnets on the remote VPN site. | In this VPN tunneling approach, VTIs are created on the NSX Edge node. Each VTI is associated with an IPSec tunnel. The encrypted traffic is routed from one site to another site through the VTI interfaces. IPSec processing happens only at the VTI. |
| DNAT is not supported on tier-0 or tier-1 gateways where policy-based IPSec VPN are configured. | OSPF dynamic routing is not supported for routing through IPSec VPN tunnels.Dynamic routing for VTI is not supported on VPN that is based on Tier-1 gateways.Load balancer over IPSec VPN is not supported for route-based VPN terminated on Tier-1 gateways. |
Use Cases of IPsec
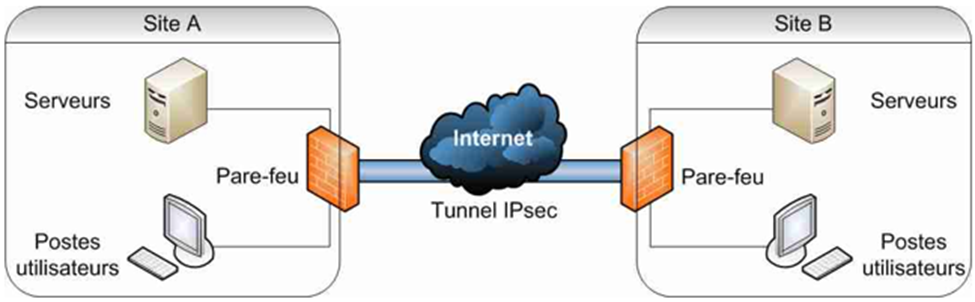
Site-to-Site VPN
IPsec enables secure connections between different locations, like branch offices and headquarters, or between a company’s network and cloud environments.
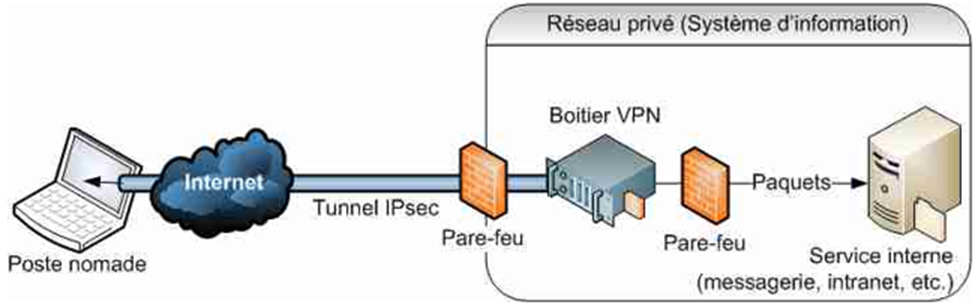
Remote access VPNs
IPsec provides secure access for remote workers to connect to their organization’s network from anywhere with an internet connection..
List of Key Security Recommendations (Extracted from ANSSI DAT-NT-003/ANSSI/SDE/NP)
• Prefer ESP protocol over AH for confidentiality, integrity, and authentication.
• Avoid manual keying and pre-shared keys (PSK) in production; use certificate-based authentication (PKI) whenever possible.
• Enable Perfect Forward Secrecy (PFS) using ephemeral Diffie-Hellman groups (preferably group 14, 15, or elliptic curve groups like ecp256/19).
• Regularly renew keys (e.g., every hour or every 100GB of data).
• Avoid weak algorithms: Do not use MD5, DES, or RSA keys <2048 bits. Prefer AES (128/256), SHA-2, and ECDSA with keys ≥256 bits.
• Enable NAT-Traversal if NAT is present between endpoints.
• Use tunnel mode for site-to-site or remote access scenarios.
• Ensure all traffic is encrypted; avoid optional IPsec policies to prevent downgrade attacks.
- Configure (IKE) parameters:
- IKE Version: IKEv2
- Encryption: AES-256
- Integrity: SHA-256
- DH Group: 14 or higher (preferably elliptic curve if supported)
- Lifetime: 1 hour
- Enable PFS
- Configure (IPsec) parameters:
- Protocol: ESP
- Encryption: AES-256
- Integrity: SHA-256
- PFS: Enable, use same DH group as Phase 1
- Lifetime: 1 hour or 100GB
Prerequisites:
- Ensure both NSX Edge devices are reachable and have public IP addresses.
- Exchange public keys/certificates if using PKI.
- Define the internal networks to be protected.
- The Tier-0 or Tier-1 gateway must be in Active-Standby high-availability mode when used for an IPSec VPN service.
- You must have at least one tier-0 or tier-1 gateway configured and available for use.
- When configuring NSX with both NAT and IPSec, it is important to follow the correct sequence of steps to ensure proper functionality. Specifically, configure NAT before setting up the VPN connection. If you inadvertently configure the VPN before NAT, for instance, by adding a NAT rule after your VPN session is configured, the VPN tunnel status will remain down.
Note:
- IPSec VPN session is not supported between a parent Tier-0 gateway and a Tier-0 VRF gateway that is attached to this parent Tier-0 gateway.
- IPSec VPN is not supported when the local endpoint IP address goes through NAT in the same logical router that the IPSec VPN session is configured.
- Wildcard certificates are not supported for IPSec VPN.
Configuration Steps:
- Navigate to NSX Manager > Networking > VPN > VPN Services.
- You must create IPSec VPN service first before you can configure either a policy-based or a route-based IPSec VPN session.
- Select ADD SERVICE > IPSec
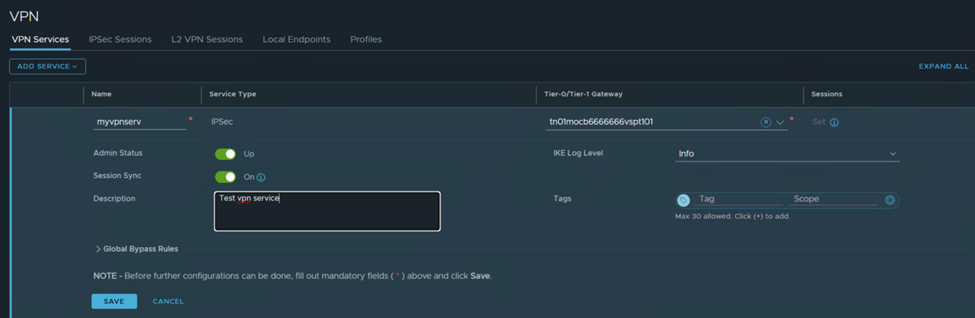
- Fill in the required parameters.
- Enter a name for the IPSec service.
- From the Tier-0/Tier-1 Gateway drop-down menu, select the Tier-0 or Tier-1 gateway to associate with this IPSec VPN service.
- Enable or disable Admin Status, by default, the value is set to Enabled.
- Set the value for IKE Log Level, the default is set to the Info level.
- Enter a value for Tags If you want to include this service in a tag group.
- To enable or disable the stateful synchronization of VPN sessions, toggle Session sync, by default, the value is set to Enabled.
- Click Global Bypass Rules if you want to allow data packets to be exchanged between the specified local and remote IP addresses without any IPSec protection. In the Local Networks and Remote Networks text boxes, enter the list of local and remote subnets between which the bypass rules are applied.
- Now click Save.
- After the new IPSec VPN service is created successfully, you are asked whether you want to continue with the rest of the IPSec VPN configuration. If you click Yes, you are taken back to the Add IPSec VPN Service panel. The Sessions link is now enabled, and you can click it to add an IPSec VPN session.
- After you have configured an IPSec VPN service, you must add either a policy-based IPSec VPN session or a route-based IPSec VPN session, depending on the type of IPSec VPN you want to configure. You also provide the information for the local endpoint and profiles to use to finish the IPSec VPN service configuration.
Create a new IPsec VPN session:
- Configure either a Policy-based or Route-based IPSec VPN session depending on your configuration preference.
- We are taking example of Policy Based IPSec Session creation.
- Navigate to the Networking > VPN > IPSec Sessions tab.
- Select Add IPSec Session > Choose either Policy Based or Route Based.
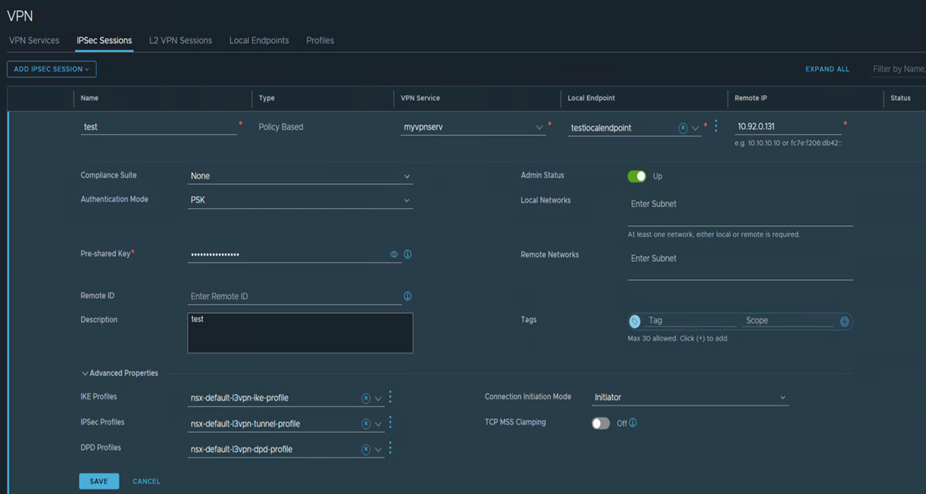
- Enter a name for the IPSec VPN session.
- From the VPN Service drop-down menu, select the IPSec VPN service to which you want to add this new IPSec session.
- Select an existing local endpoint from the drop-down menu or to create a different local endpoint, click the three-dot menu (
 ).
). - In the Remote IP text box, enter the required IP address of the remote site.
- Enter an optional description for this IPSec VPN session.
- To enable or disable the IPSec VPN session, click Admin Status.
- From the Compliance suite drop-down menu, select a security compliance suite.
- The default value selected is None. If you select a compliance suite, the Authentication Mode is set to Certificate and in the Advanced Properties section, the values for IKE profile
and IPSec profile are set to the system-defined profiles for the selected security compliance suite. You cannot edit these system-defined profiles. Specify local and remote endpoint IP addresses. - If the Compliance Suite is set to None, select a mode from the Authentication Mode drop-down menu.
The default authentication mode used is PSK, which means a secret key shared between NSX Edge and the remote site is used for the IPSec VPN session. If you select Certificate, the site certificate that was used to configure the local endpoint is used for authentication. - In the Local Networks and Remote Networks text boxes, enter at least one IP subnet address to use for this policy-based IPSec VPN session (In CIDR format).
- If Authentication Mode is set to PSK, enter the key value in the Pre-shared Key text box
- To identify the peer site, enter a value in Remote ID.
- To change the profiles, initiation mode, TCP MSS clamping mode, and tags, click Advanced Properties.
- Click Save.
- Once the configuration is successfully completed, you would see “Success” status.
- Test connectivity and ensure only encrypted traffic is allowed between sites.