Managing SSL Certificates on FE ELB
Managing SSL certificates on FlexibleEngine Cloud can be a complex and time-consuming task, but it is crucial for ensuring the security and trustworthiness of your website or application. SSL certificates encrypt the data exchanged between the server and the client, preventing eavesdropping and tampering, and providing a way to verify the identity of the server.
One of the main challenges of managing SSL certificates is ensuring the continuity and availability of your SSL certificates. If a certificate expires or becomes invalid, your website or application may become inaccessible or untrusted, leading to loss of revenue, reputation, or data. and it is up to you to act promptly and replace the affected certificates. You may also need to plan for disaster recovery scenarios, such as restoring backups or migrating to alternative domains or providers.
To manage SSL certificates on the cloud effectively, you need to follow some best practices. First, you should always use strong and unique passwords or keys to protect your certificates and private keys. You should also configure your servers to use the latest TLS protocol versions and ciphers, and to enable HTTP Strict Transport Security (HSTS) to prevent downgrade attacks. Additionally, you should monitor your SSL certificates regularly and renew them before they expire, using automated or manual methods as appropriate.
Code Github repository : https://github.com/FlexibleEngineCloud/fe-letsencrypt
Diagram
This documentation is a step-by-step guide to create and renew Let’s Encrypt SSL certificates on FlexibleEngine Cloud on “Elastic Load Balancer” ELB using Certbot linux utility.
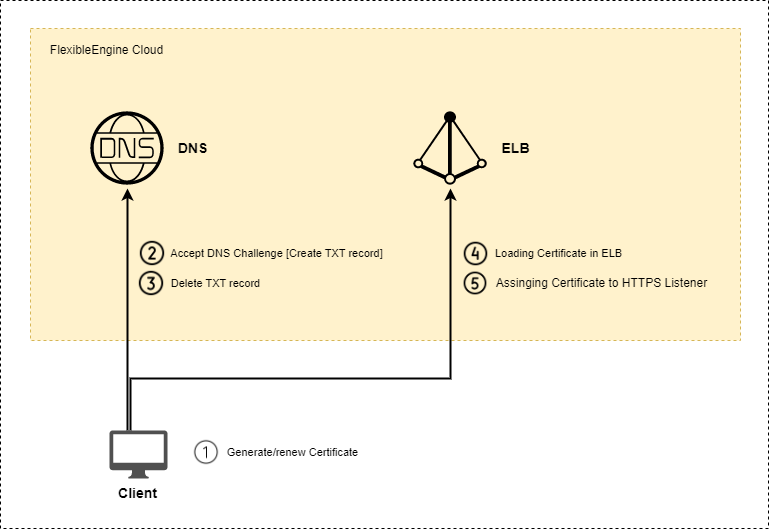
Prerequisites
Before you begin, you’ll need to make sure you have the following:
- A Flexible Engine account.
- A domain name registered and managed on FlexibleEngine DNS service
- A DNS Record of type A already created on DNS Service.
- An ELB Listener along with an HTTPS Listener.
- A server where you will run the bash scripts and install Certbot utility
Step 1: Install Certbot
The first thing you need to do is install Certbot, which is the tool we will use to create and renew SSL certificates. Certbot is available for most popular Linux distributions, and you can find detailed installation instructions on the Certbot website: https://certbot.eff.org/instructions
For example, if you are using Ubuntu, you can install Certbot by running the following commands:
sudo apt-get update
sudo apt-get install certbot
Step 2: Setting environment variables
Next, you must set environment-variables.sh bash script, this includes:
- Authentication credentials
- FE region
- FE domain name
- FE project ID
- DNS domain name
- dns zone ID
- HTTPS Listener ID
- ELB Elastic IP address
- Certificate name
Step 3: Create the first certificate
Now that you have Certbot installed and you setted environment variables in environment-variables.sh , you can create your first SSL certificate.
You can use the following bash command to run the script:
./create.sh
Certbot allows for the specification of pre and post validation hooks when run in manual mode. The flags to specify these scripts are –manual-auth-hook and –manual-cleanup-hook respectively.
This will run the authenticator.sh script, attempt the validation, and then run the cleanup.sh script. Additionally Certbot will pass relevant environment variables to these scripts:
- CERTBOT_DOMAIN: The domain being authenticated
- CERTBOT_VALIDATION: The validation string
- CERTBOT_TOKEN: Resource name part of the HTTP-01 challenge (HTTP-01 only)
- CERTBOT_REMAINING_CHALLENGES: Number of challenges remaining after the current challenge
- CERTBOT_ALL_DOMAINS: A comma-separated list of all domains challenged for the current certificate
The –manual-auth-hook option allows you to specify a shell command to be run after the user completes the manual steps required for authentication, but before Certbot proceeds with obtaining the certificate. This is useful if you need to perform additional steps, for this example to complete the authentication process by accepting the DNS challenge on Flexible Engine DNS Service.
The –manual-cleanup-hook option allows you to specify a shell command to be run after the certificate has been successfully obtained and installed, but before Certbot exits. This is useful if you need to perform additional cleanup steps, for this example deleting the DNS record that was created during the authentication process when accepting the DNS challenge.
More details, please refer to certbot documentation: https://eff-certbot.readthedocs.io/en/stable/using.html
Step 4: Renew the certificate
SSL certificates expire after a certain period, so you will need to renew them periodically. You can use the following bash command to run the script:
./renew.sh
The renew.sh script will attempt to renew certificate previously obtained for the specified domain. and load it to Flexible Engine ELB (domain, and auth credentials… will be retrieved from env variables script)
To automatically renew the certificate after a specific period of time in a regular way, you could use Cron jobs to automate the execution of renew.sh bash script.
Cron job is a time-based job scheduler in Unix-like operating systems. It is used to schedule commands or scripts to run automatically at specific times and dates on the server. Cron is very useful for automating repetitive tasks.
As an example:
0 0 1 JAN,APR,JUL,OCT * /path/to/renew.sh
This cron job will run the script renew.sh at midnight on the first day of January, April, July, and October every year.
0: The minute when the job should run (in this case, 0, which means midnight)0: The hour when the job should run (in this case, 0, which means midnight)1: The day of the month when the job should run (in this case, the first day of the month)JAN,APR,JUL,OCT: The months when the job should run (in this case, January, April, July, and October)/path/to/renew.sh: The command or script that should be executed
In conclusion, creating and renewing SSL certificates with Let’s Encrypt and Certbot is a relatively straightforward process that can provide secure encryption for your website or application. By following the steps outlined in this documentation, you can obtain and install SSL certificates quickly and easily on your Flexible Engine ELB, ensuring that your website visitors’ data remains safe and secure.
It is important to remember to keep your SSL certificates up to date and renew them before they expire to maintain uninterrupted HTTPS protection. renew.sh automated renewal process can simplify this task and ensure that your certificates remain valid without any manual intervention.